The Autonomous Data Warehouse Cloud (ADWC) service provides a Service Console that can be used to monitor the service activity and to carry out a small number of administration tasks (e.g. changing some resource management rules).
The documentation specifically says to use the ADMIN user to login. But, actually, any unlocked database user having the CREATE SESSION privilege can be used to login. This is not only useful, but, in my opinion, necessary. In fact, developers should be able to see the service activity without knowing the password of the ADMIN user.
The documentation provides no information about what privileges are needed to take advantage of the provided functionalities. If you login with a user having only the CREATE SESSION privilege you get either empty charts or errors when trying to use some of the functionality. The following figure illustrates:
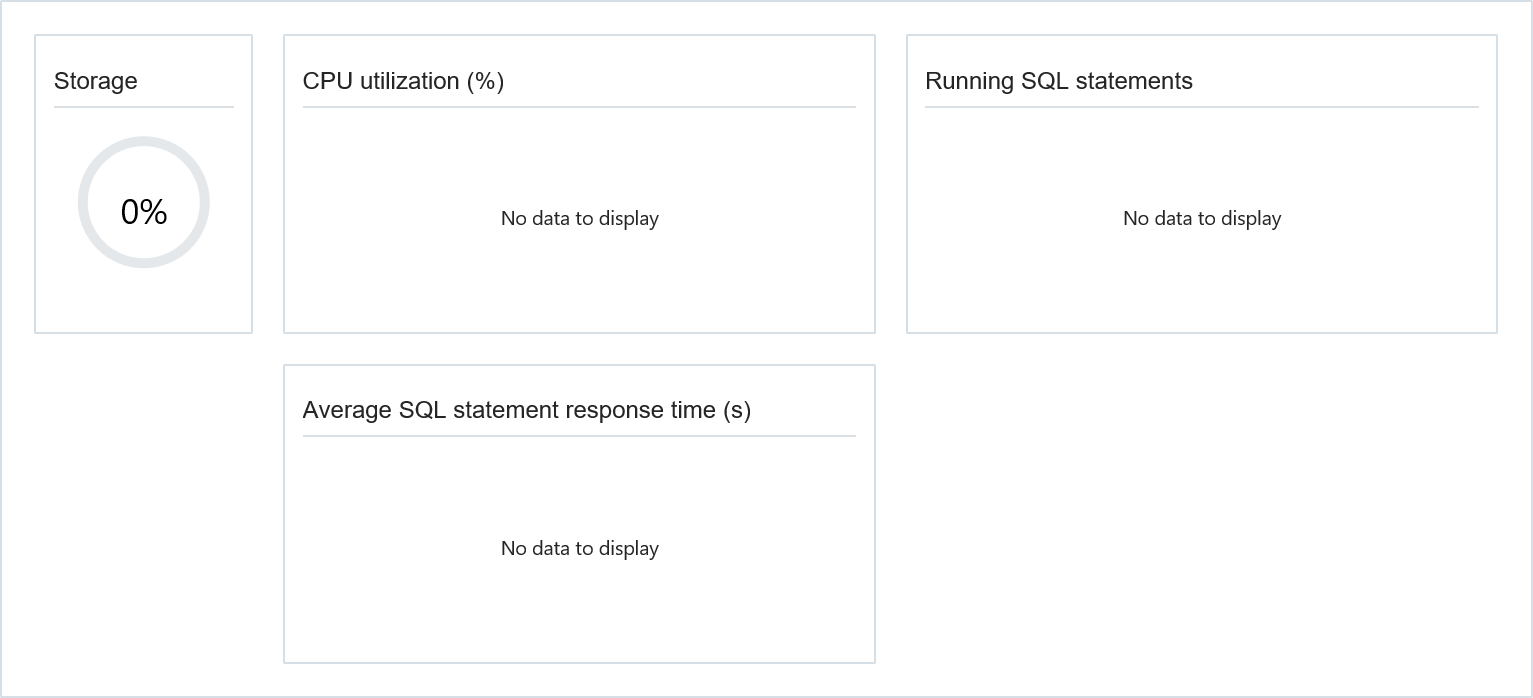
In other words, the UI is static and privileges are only checked when a specific functionality is used. I would expect something dynamic…
By looking at the roles owned by the ADMIN user, I noticed three roles with a name that could match what I was looking for: CONSOLE_MONITOR, CONSOLE_OPERATOR and CONSOLE_ADMIN. Then, with some trial and error, I came up with the following table that summarizes which role provides which functionality:
| Functionality | CONSOLE_MONITOR | CONSOLE_OPERATOR | CONSOLE_ADMIN |
|---|---|---|---|
| Overview | No data | Data visible | Data visible |
| Activity | No data | Data visible | Data visible |
| Activity – Cancel execution | Unauthorized | Authorized | Authorized |
| Administration – Download Client Credentials | Unauthorized | Authorized | Authorized |
| Administration – Set Resource Management Rules | Unauthorized | Authorized | Authorized |
| Administration – Set Administrator Password | Unauthorized | Unauthorized | Authorized |
| Administration – Manage Oracle ML Users | Unauthorized | Unauthorized | Authorized |
| Administration – Download Oracle Instance Client | Authorized | Authorized | Authorized |
| Administration – Send Feedback to Oracle | Authorized | Authorized | Authorized |
Notes:
- A user with the CONSOLE_MONITOR role has the same privileges than a user without any role. To me this state of affairs do not look correct. I would expect that the CONSOLE_MONITOR role makes visible the Overview and Activity data.
- With these roles it is not possible to provide only the privileges to see data without being able to modify something or kill sessions.
- The “Cancel execution” functionality is actually a “kill session”. My guess is that as soon as the service is upgrade to 18c then new functionality to cancel executions will be used instead.